LTIMindtree’s Mobile Threat Defense Service
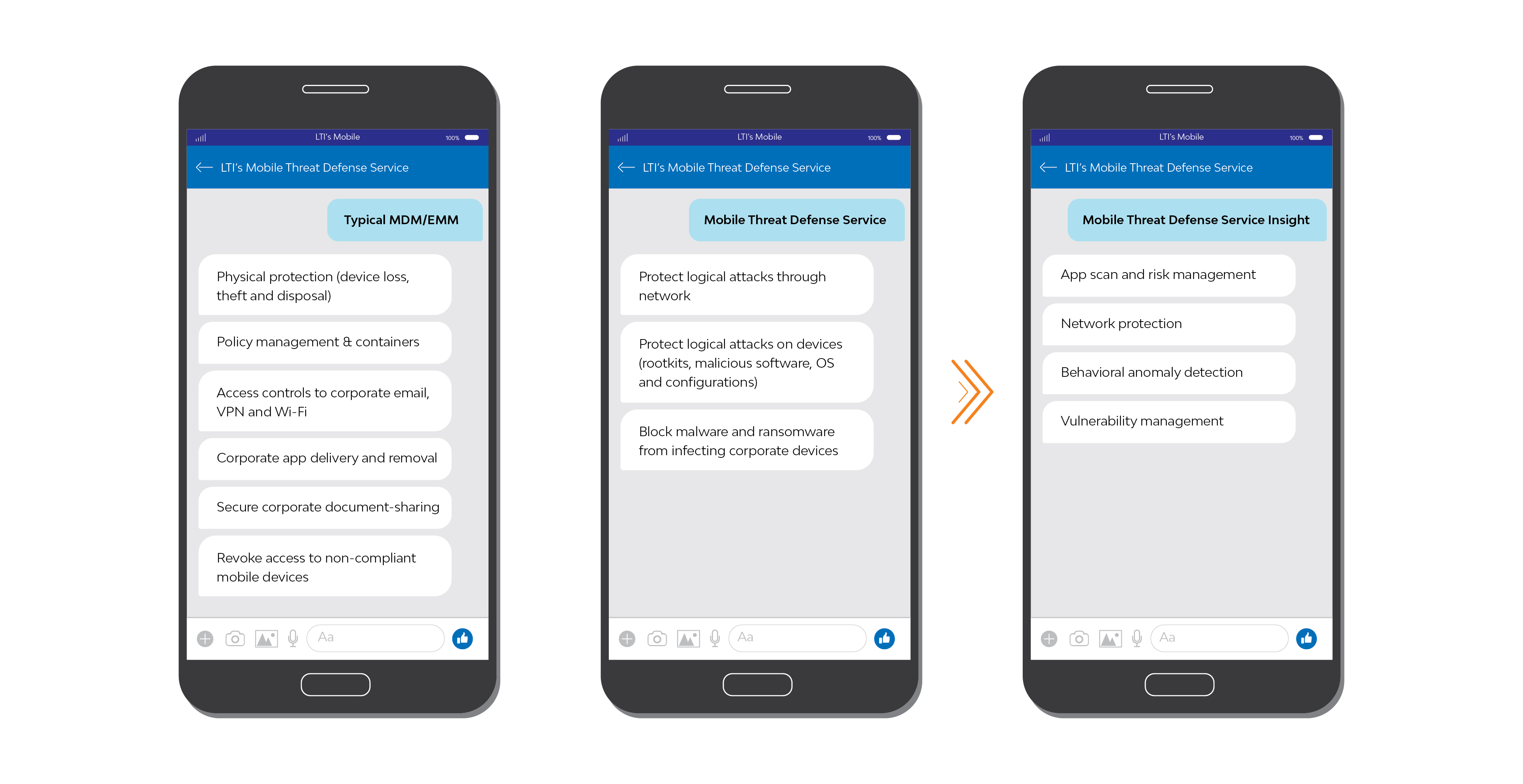
Many organizations aren’t fully prepared to deal with the security challenges posed by the proliferation of mobile devices. Increasing mobile device features and affordable connectivity has led to extensive usage of mobile devices for accessing corporate data & applications. Increase in the number of malware and phishing attacks on smartphones, rootkits and trojans, network and configuration-based attacks, application threats, etc., pose a very high security risk to the security of the mobile device and thereby the corporate data. Traditional MDM solutions need to be complimented with additional protection & monitoring. This is where LTIMindtree’s Mobile Threat Defense Service steps in. LTIMindtree’s Mobile Threat Defense Service delivers 24X7 protection through its state-of-the-art cyber defense resiliency centers (CDRC) across the globe on a real-time basis. CDRC protects your BYOD and corporate-owned iOS, Android and Windows mobile devices (managed and unmanaged), from the full range of mobile threats. Our technology & platform-driven service gives you the ability to dynamically detect and prescribe remediation for known and unknown threats. LTIMindtree’s Mobile Threat Defense Services involves installation of an “ActiveShield” app that runs seamlessly on your mobile device (Apple iOS, Android or Windows), identifying and automatically protecting from malicious applications, rogue WiFi networks, device threats and OS vulnerabilities etc. with complete monitoring & remediation support from the CDRC across the globe.
Reach us
Key Highlights
- Trusting corporate data, IP & other resources will be safe in the cloud, and enterprises need a comprehensive security strategy around Office 365.
- Visibility into the enterprise’s mobile security posture, and collection of mobile threat intelligence.
- Extend Corp DNS Firewall rules to the end-points, accessing corporate resources over the Wi-Fi network.
- Implement risk-based conditional access – Ensure only safe mobile devices have access to corporate resources such as Office 365, SharePoint Online and OneDrive for Business.
- Protect apps from tampering & reduce mobile fraud.
Key Benefits
- Protect devices from emerging mobile threats.
- Real-time visibility of active mobile threats, targeted attacks and vulnerabilities, which may be compromising your covered devices, whether workforce managed or BYOD.
- Non-invasive end-user experience, with minimal storage and battery usage.
- Harness predictive intelligence, crowd source and research, to build a living picture of mobile threats 24X7, from virtually anywhere in the world.
- Centralized risk, security and compliance management.
- Simple EMM integration to automatically enforce the corporate security policy, for covered mobile devices under attack.




