Regulatory Pressure Meets Operational Reality: Critical Infrastructure Cybersecurity
The digital arteries of modern life, energy grids, water systems, transport networks, and manufacturing lines are more connected than ever. This connectivity fuels efficiency and innovation but also opens the door to escalating cyber risks.
As IT and OT systems converge and IoT devices proliferate across industrial environments, the attack surface has expanded dramatically. This has made sectors like energy, water, transportation, and manufacturing increasingly vulnerable to sophisticated cyber threats.
Over the past few years, breaches targeting operational technology (OT), industrial control systems (ICS), and IoT ecosystems have surged. These incidents have exposed systemic weaknesses and prompted urgent calls for reform.
Current status: Attack surface and regulatory environment
The attack surface for critical infrastructure grows almost every day. The convergence of IT and OT, the rapid adoption of IoT, and vulnerabilities in legacy systems have led to a spike in both the frequency and sophistication of cyberattacks. Recent incidents targeting water treatment plants, electrical grids, and transportation networks are stark reminders of these rising threats.
Globally, regulators are responding decisively. Key developments shaping cybersecurity best practices in 2025 include:
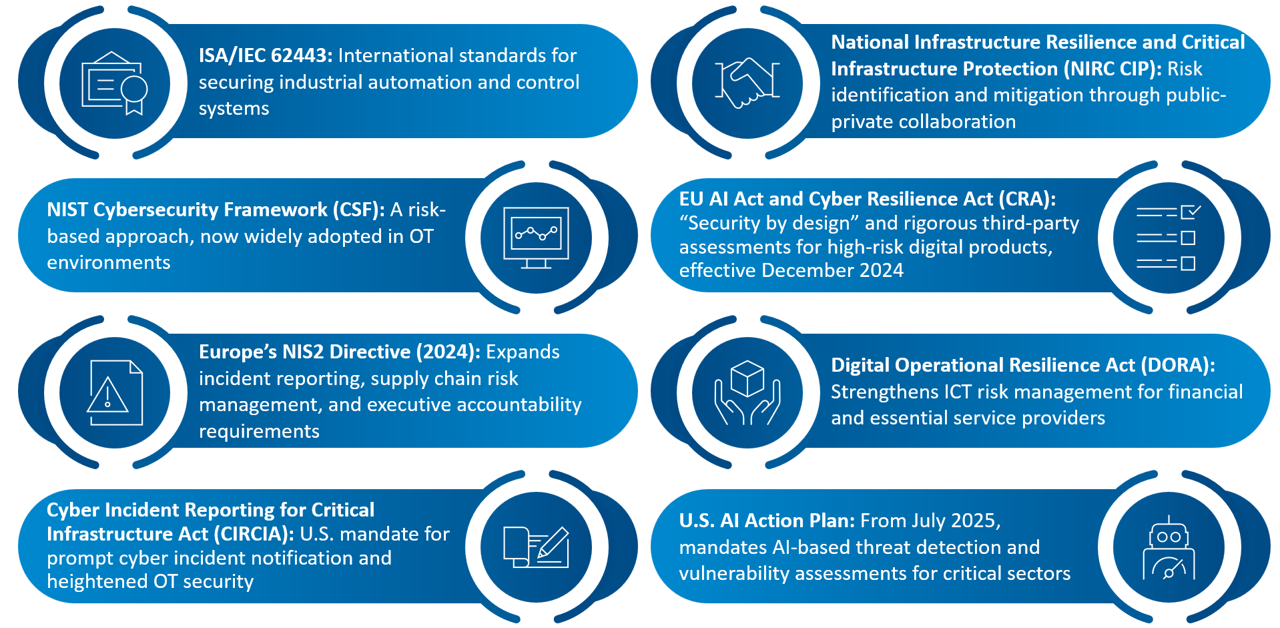
Countries across Asia, such as India, Singapore, and Japan, are also issuing sector-specific mandates, especially for energy, health, and manufacturing while aligning closely with these global standards.
Is compliance alone enough?
Regulations provide a foundation for securing critical infrastructure. But do they deliver true resilience?
Compliance, by its nature, is reactive and focuses on meeting minimum standards and passing audits. Therefore, they often fall short of delivering true cyber resilience. However, the threat landscape in OT/ICS and IoT environments is dynamic, with adversaries constantly evolving their tactics to exploit vulnerabilities in legacy systems, supply chains, and human processes.
Too often, organizations operate under the misconception that being compliant equals being secure. This mindset leads to what is often called checkbox security, where controls are implemented merely to satisfy auditors rather than to mitigate real-world risks. In practice, this can result in fragmented defenses, outdated incident response plans, and a lack of visibility into OT-specific threats.
Moreover, compliance frameworks often lag behind emerging technologies and attack vectors. For example, while regulations may mandate network segmentation or access controls, they rarely address the nuances of securing smart sensors, remote access tools, or AI-driven industrial automation.
To truly protect critical infrastructure, organizations must go beyond compliance. This means adopting a risk-based approach, integrating cybersecurity into operational workflows, and fostering a culture of continuous improvement. Cyber resilience is a continuous journey that requires proactive investment, cross-functional collaboration, and a commitment to staying ahead of the curve.
Best practices for compliance and resilience
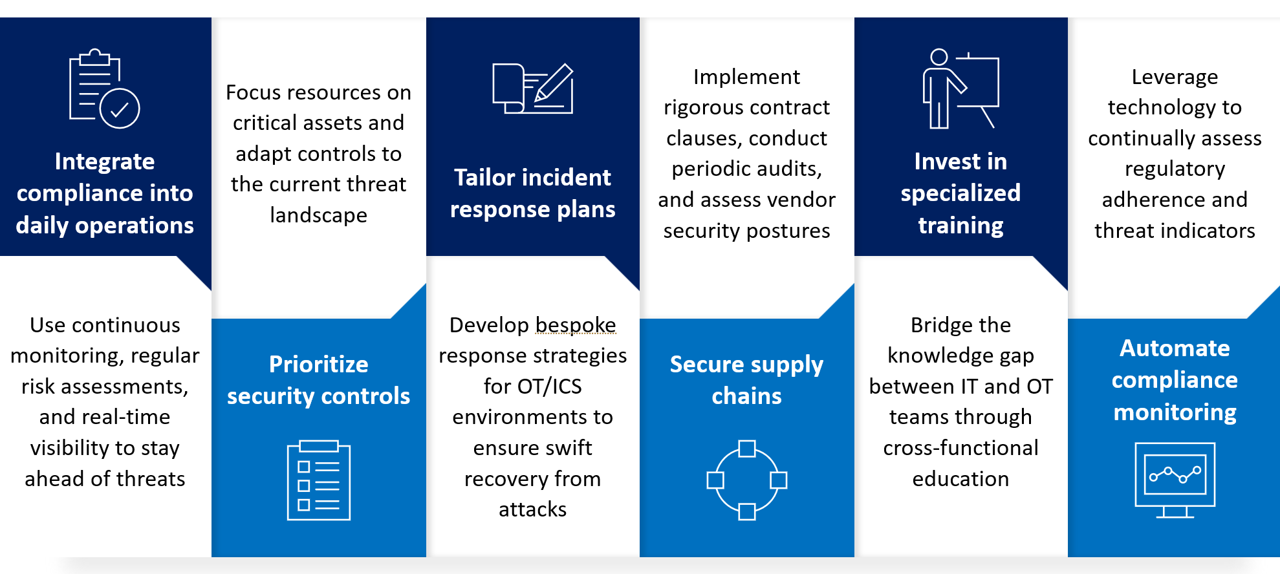
To build true resilience in critical infrastructure, organizations must integrate compliance into daily operations through ongoing monitoring and risk assessments. Prioritizing controls based on asset importance and current threats, enhancing incident response tailored to OT/ICS environments, securing the supply chain with robust vendor agreements, and investing in specialized cross-functional training are all essential steps. These practices go beyond mere checkbox compliance, embedding cybersecurity as an active, continuous process.
What is the appropriate strategy?
Given the many overlapping requirements, organizations are increasingly focused on harmonizing their compliance efforts. Integrating NIRC CIP and global frameworks is now crucial for meeting regulatory demands and ensuring that critical infrastructure can withstand and recover from cyber threats.
However, compliance is only the first step. True resilience requires embedding cybersecurity into daily operations, breaking down silos between IT and OT departments, and fostering a culture of proactive risk management and continuous improvement.
To move beyond checkbox compliance and embrace real resilience, my core recommendations are:
Barriers and success stories: Observations
Organizations striving for resilience often face considerable obstacles. These include outdated legacy systems lacking robust security features, disjointed approaches arising from siloed IT and OT teams, an emphasis on documentation over practical security measures, inconsistent standards among third-party vendors, and a shortage of professionals with deep expertise in both cybersecurity and OT/ICS. Yet, there are notable success stories.
For example, a European energy provider synchronized its compliance initiatives with NIS2 and ISA/IEC 62443 standards, invested heavily in workforce training and automated threat detection. The result: passing regulatory audits while reducing incident response times by 60%.
Similarly, a major Asian manufacturer upgraded its legacy infrastructure with secure remote access and network segmentation. By integrating IT and OT incident response protocols, it effectively contained a ransomware attack without any operational downtime.
How organizations can strengthen resilience
Across industries, leading organizations are taking a systematic approach to strengthening infrastructure resilience—evaluating systems against both regulatory requirements and recognized best practices. This often involves creating a clear roadmap, then implementing the right mix of controls, tools, and technologies to bolster defenses and ensure operational continuity.
LTIMindtree is among the organizations enabling this transformation, evaluating resilience across sectors, guiding stakeholders, and embedding the safeguards needed for long-term protection.
Conclusion
As regulatory frameworks evolve to match the sophistication of cyber threats, critical infrastructure organizations must shift from reactive compliance to proactive resilience. This journey demands more than passing audits; it requires a holistic, risk-based approach that integrates security into every facet of operations.
The efforts of forward-thinking companies have shown that, with the right strategies and collaboration, it is possible to protect the most critical assets, ensuring security, continuity, and public trust for years to come.
References
- Cybersecurity Regulations: Industry Perspectives on the Impact, Progress, Challenges, and Opportunities of Harmonization, Gavo.gov, Jul 30, 2025: https://www.gao.gov/products/gao-25-108436
- 5 Key OT Cybersecurity Strategies from the WEF Global Cybersecurity Outlook 2025, Jonathon Gordon, Industrialcyber.co, Jan 19, 2025: https://industrialcyber.co/news/5-key-ot-cybersecurity-strategies-from-the-wef-global-cybersecurity-outlook-2025/
- Five Trends Driving OT Cybersecurity in 2025, George V. Hulme, Nexusconnect.io, Jan 9, 2025: https://nexusconnect.io/articles/five-trends-driving-ot-cybersecurity-in-2025
More from Rangappa Halagani
As a cybersecurity consultant specializing in OT, IoT and IT, the transformative power of technology…
Latest Blogs
Introduction There is a lot of noise around Agentic AI right now. Every headline seems to…
Traditionally operations used to be about keeping the lights on. Today, it is about enabling…
Generative AI (Gen AI) is driving a monumental transformation in the automotive manufacturing…
Organizations are seeking ways to modernize data pipelines for better scalability, compliance,…




